ICMP full name Internet Control Message Protocol
Some people may feel strange when it comes to ICMP. In fact, ICMP is closely related to us. In all levels of the network architecture, control is required, and different levels have different division of labor and control content. The IP layer control function is the most complex, mainly responsible for error control, congestion control, etc. Any control is established in On the basis of information, in the network system based on IP datagram, the gateway must handle the transmission of datagrams by itself, and the IP protocol itself has no intrinsic mechanism to obtain error information and process. In order to deal with these errors, TCP/IP designed the ICMP protocol. When a gateway finds a transmission error, it immediately sends an ICMP message to the source host, reports the error message, and causes the source host to take appropriate action. It is an error. And control message protocol, not only for transmitting error messages, but also for transmitting control messages.
ICMP packet formatThe first 4 bytes of all IC MP messages are the same, but the remaining bytes are different from each other. .
The type field can have 15 different values ​​to describe a particular type of ICMP message. Some ICMP messages also use the value of the code field to further describe the different conditions.
Indicates the data structure of the ICMP header
Typedefstruct icmp_hdr
{ unsigned char icmp_type; //message type
Unsigned char icmp_code; //code
Unsigned short icmp_checksum; //checksum
Unsigned short icmp_id; //ID number
Unsigned short icmp_sequence; //serial number
Unsigned long icmp_TImestamp; //timestamp
} ICMP_HDR, *PICMP_HDR;
Type of ICMP packetICMP is often considered an integral part of the IP layer, passing error messages and other information that requires attention. ICMP messages are typically used by IP layers or higher layer protocols (TCP or UDP). ICMP messages are transmitted inside IP datagrams. The IP protocol is an unreliable protocol. It cannot guarantee that an IP datagram can successfully reach the destination host and cannot perform error control. The ICMP protocol can assist the IP protocol to perform these functions. The following is the data structure of the ICMP message:
Type: An 8-bit type field indicating the ICMP packet type;
Code: An 8-bit code field that represents a function in the specified type. If there is only one function in a type, the code field is set to 0.
Checksum: A 16-bit checksum on the ICMP part of the packet;
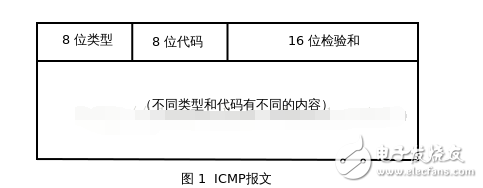
When an error message is sent, the message always contains the IP header and the first 8 bytes of the IP datagram that generated the ICMP error message. In this way, the module receiving the ICMP error message will associate it with a specific protocol (based on the protocol field in the IP datagram header) and the user process (based on the TCP included in the first 8 bytes of the IP datagram). Or the TCP or UDP port number in the UDP packet header to determine).
The following conditions do not result in an ICMP error message:
ICMP packet error (ICMP query packet may generate ICMP error packet);
The destination address is an IP datagram of a broadcast address or a multicast address;
a datagram broadcast as a link layer;
Not the first piece of IP fragmentation;
The source address is not a datagram of a single host, that is, the source address cannot be a zero address, a loopback address, a broadcast address, or a multicast address;
The following is an analysis of the types of ICMP error messages:
1. ICMP target unreachable message: When the IP router cannot send an IP datagram to the destination address, it will return a target unreachable ICMP message to the sender host, and display the specific reason for the unreachability in this message.
2. ICMP redirect message: If the router finds that the sender host sends data using the suboptimal path, it will return an ICMP redirect message to the host. This message contains the most appropriate routing information and source data. The main reason is that when the router holds better routing information, the router will send a more suitable sending route to the sending host through the ICMP redirect message.
3. ICMP timeout message: There is a field TTL (TIme to live) in the IP packet. Its value is decremented by 1 every time it passes through a router, until it is discarded, the IP packet is discarded. At this point, the IP router will send an ICMP timeout message to the sending host and notify the packet that it has been dropped.
4. Source Suppression Message: When the TCP/IP host sends data to another host, if the speed reaches the saturation state of the router or link, the router sends an ICMP source suppression message.
The various types of ICMP messages are shown in the figure, and the different types are determined jointly by the type field and the code field in the message. The last two lists in the figure indicate whether the ICMP message is a query message or an error message. Because ICMP error messages sometimes require special handling, we need to distinguish them. For example, when responding to an ICMP error message, another ICMP error message will never be generated (if there is no such restriction rule, an error may be encountered to generate another error, and the error generates an error again. Will cycle endlessly).
When sending an ICMP error message, the message always contains the first 8 bytes of the IP header and the IP datagram that generated the ICMP error message. In this way, the module receiving the ICMP error message will associate it with a specific protocol (based on the protocol field in the IP datagram header) and the user process (based on the TCP included in the first 8 bytes of the IP datagram). Or the TCP or UDP port number in the header of the UDP packet to judge). 6 . Section 5 will give an example to illustrate.
The following conditions will not result in an ICMP error message:
1) ICMP error message (however, ICMP query message may generate ICMP error message).
2) The destination address is an IP datagram of a broadcast address or a multicast address.
3) Datagrams broadcast as link layers.
4) Not the first piece of IP fragmentation.
5) The source address is not a single host's datagram. That is to say, the source address cannot be a zero address, a loopback address, or a broadcast place.
Address or multicast address.
These rules are intended to prevent broadcast storms that in the past allowed ICMP error messages to respond to broadcast packets.
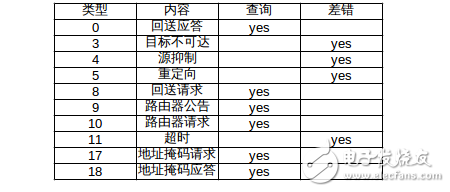
Here are a few common ICMP messages:
Response request
The ping that we use most daily is the response request (Type=8) and the response (Type=0). One host sends a Type=8 ICMP message to a node. If there is no abnormality on the way (for example, it is discarded by the router, the target If the switch does not respond to ICMP or the transmission fails, the target returns an ICMP packet with Type=0, indicating that the host exists. The more detailed tracert determines the network distance between the host and the target by calculating the node through which the ICMP packet passes.
2. Target unreachable, source suppression and timeout messages
The format of the three types of messages is the same. The target unreachable message (Type=3) is used when the router or the host cannot transmit the datagram. For example, if we want to connect to a non-existent system port (the port number is less than 1024), Will return Type=3, Code=3 ICMP message, it tells us: "Hey, don't connect, I am not at home!", common unreachable types and network unreachable (Code=0), host Unreachable (Code=1), protocol unreachable (Code=2), etc. Source suppression acts as a control traffic. It notifies the host to reduce the data traffic. Since ICMP does not recover the transmitted packets, the host will gradually resume the transmission rate as long as the packet is stopped. Finally, the problem with the connectionless network is that the datagram will be lost, or the network will be roamed for a long time and the target cannot be found, or the congestion will cause the host to reassemble the datagram segment within the specified time. At this time, the ICMP timeout packet will be triggered. The production. The code field of the timeout message has two values: Code=0 indicates the transmission timeout, and Code=1 indicates the reassembly segment timeout.
3. Time stamp
The timestamp request message (Type=13) and the timestamp response message (Type=14) are used to test the transmission time of the datagram between the two hosts. During transmission, the host fills in the original timestamp. After receiving the request, the receiver fills the receiving timestamp and returns it in the format of Type=14. The sender calculates this time difference. Some systems do not respond to such messages.
The push-back pallet rack means that when the forklift stores the goods arriving after the forklift into the rack from the front, the goods will push the original goods to the rear. When picking up goods from the front, since the rack slide rails are inclined forward, the goods in the rear automatically slide to the front for picking.
Features:
1. The storage density is high, but the accessibility is poor. Generally, there are 3 storage positions in the depth direction, and up to 5 storage positions.
2. It saves one third of the space than the general pallet rack and increases the storage space.
3. Suitable for general forklift access.
4. It is suitable for the storage of small varieties and large quantities of items.
5. Storage of items that are not too heavy.
6. The goods automatically slide to the front storage position.
7. No FIFO access.
Push-Back Pallet Racks,Push-Back Pallet Shelves For Storage,Pallet Racking Efficient Access,Pallet Racking No Aisles Needed
Wuxi Lerin New Energy Technology Co.,Ltd. , https://www.lerin-tech.com